FEATURES
Proactively Manage Threats with Real-Time Vulnerability Management
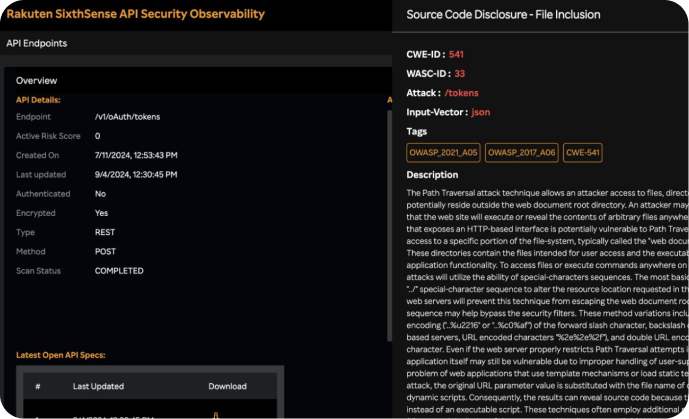
Monitor API endpoints in real time, prioritizing vulnerabilities based on severity and business impact. Automatically apply virtual patches, reducing response times and operational risks. Detect and mitigate vulnerabilities before they are exploited. Gain Full Visibility into API Attacks
Capture comprehensive details about events, incidents, and attacker behavior. Correlate related events to detect advanced attacks and understand the attacker’s sequence of actions. Identify the source of attacks quickly for faster mitigation and reduced investigation times. Automate Responses with Triggers and Alerts
Surface critical issues through configurable, automated triggers based on exploit severity and API risk. Execute real-time responses like attack blocking, targeted rate limiting, and virtual patching to stop threats before they escalate. Prioritize incident response using AI-driven alerts and reduce manual intervention. Active Threat Detection with AI-Driven Traffic Monitoring
Real-time tools analyze API traffic, identifying anomalies and threats. Advanced machine learning filters out malicious activities from legitimate traffic, preventing risks before they impact your system. Secure microservices by addressing unusual behavior patterns before they cause harm. Enhance Control with Automated API Discovery and Documentation
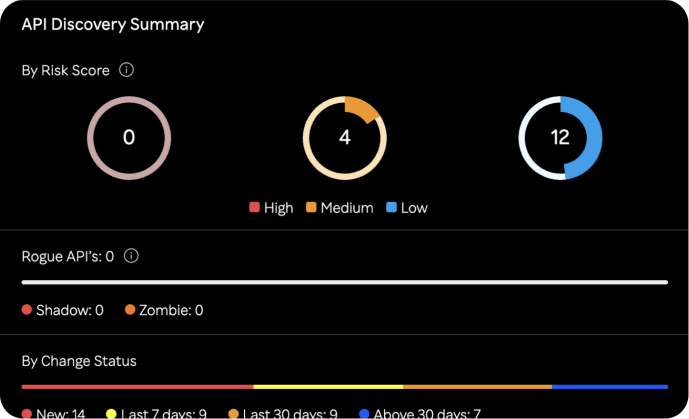
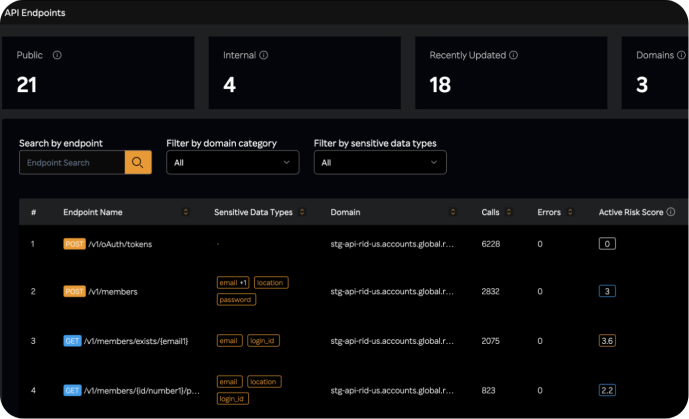
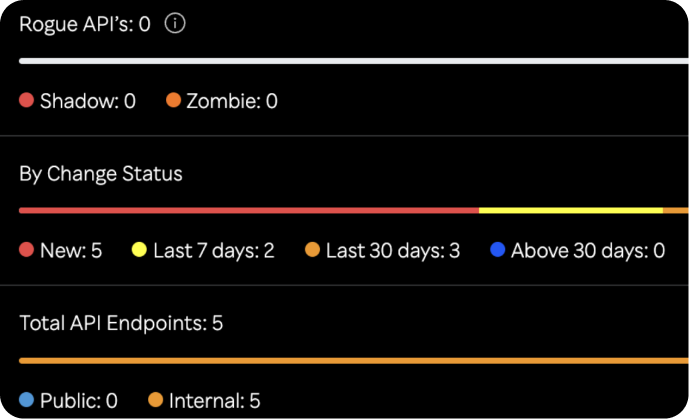
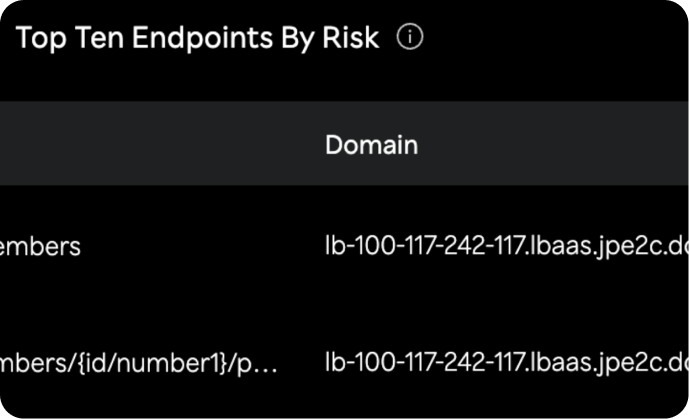
Automatically generate and update API inventories for real-time documentation. Continuously discover API endpoints, hosts, and domains to ensure comprehensive visibility. Integrate with existing DevOps, security, and IT tools for seamless operations and compliance reporting. Secure Sensitive Data with Continuous PII Exposure Detection
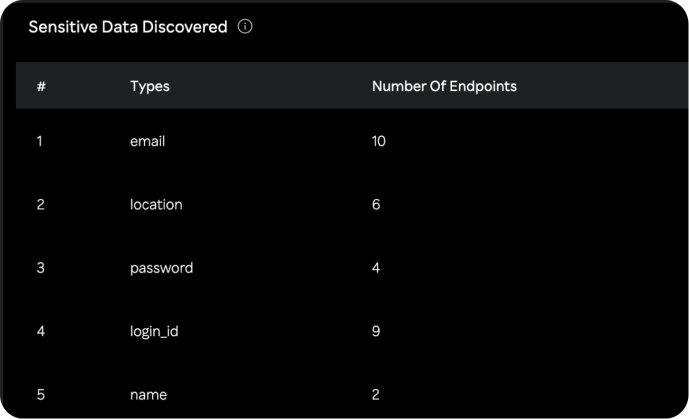
Continuously monitor API data flows to detect and prevent PII exposure. Instantly identify sensitive data leaks and address potential compliance issues. Ensure secure data handling across APIs and third-party services with proactive monitoring.